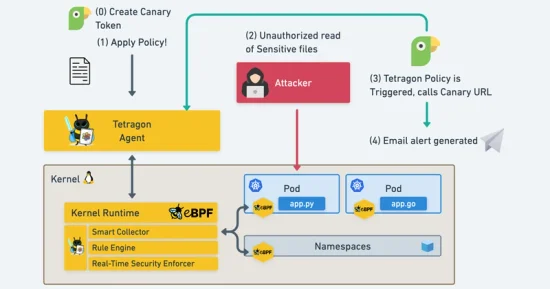
Tutorial: Setting Up a Cybersecurity Honeypot with Tetragon to Trigger Canary Tokens
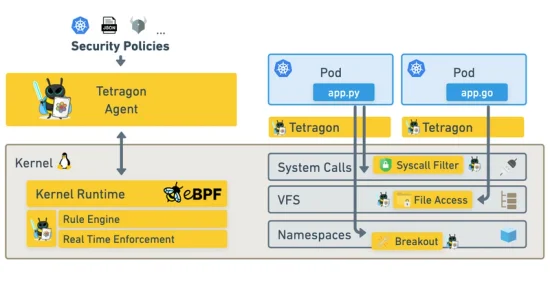
Learn how Tetragon, through eBPF, interrogates kernel level events to provide alert triggering options, aiding in the creation of a cybersecurity honeypot for better system protection